Application Security Posture Management and You
March 14, 2024 •Alistair Pugin

Ahead of next week's Guidance for Successful ASPM in Entra ID webinar, I want to discuss what ASPM is and why it's critical to the security of your organization. First, some background...in a previous life, I worked for a dev shop that built enterprise-grade multi-scale cloud-native applications for banks, telcos, etc., using languages like Python and PHP to deliver rich user experiences with complex functionality.
Funnily enough, the conversation about security and vulnerabilities was not high on their list of priorities. They did hint at using platforms like SonarQube for code quality with the possibility of it also detecting vulnerabilities.
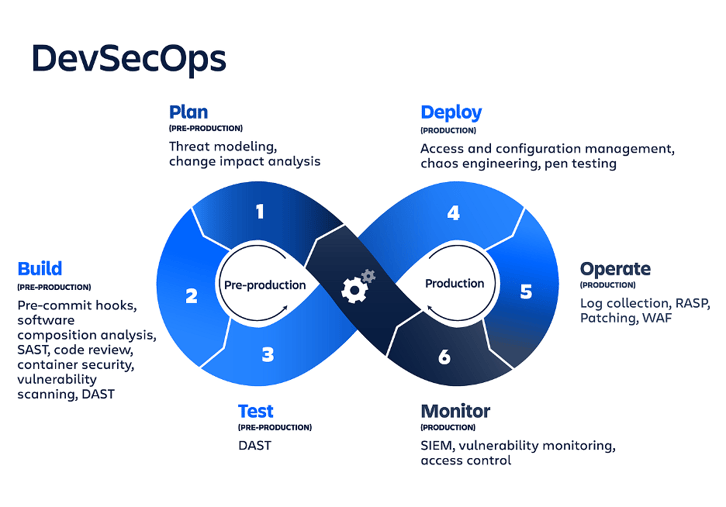
Figure 1. DevSecOps (Source: https://www.featbit.co/blogs/DevSecOps-With-Feature-Flags)
Having said that, DevSecOps was and still is a thing. But like with SRE (Site Reliability Engineering), it’s all about positioning what the concept is and, most importantly, who is responsible for what it does.
In this case, because identity admins “own” Entra, there’s this little thing called Application Registrations/Enterprise Applications that is very new to most identity people. You see, in the old days, the identity admins did not have to worry about the application's security. This was for the security people. They used to sit in another building, thinking about things like firewalls and ports, patching and hardening.
But that world has become grey. The grey that is Entra ID. The grey that has all these words and abbreviations that either end or begin with the word “Application.” And because of that word, and our famous other term, “posture,” naturally, like all things IT, we have a convergence. A meeting of the minds, a blending of the forces that are applications and posture, sprinkled with the ever so gentle use of the term “security.” Gentle use should be read in my sarcasm font. The same font I used to instill the fear of God into my kids.
“And I will strike down upon thee, with great vengeance and furious anger…” Ezekiel 25:17, also known as the Samuel L. Jackson quote from Pulp Fiction.
Application Security Posture Management (ASPM) must be viewed in very much the same light as Mr. Jackson’s character in the movie. If you do not practice ASPM in your organization, you will face the wrath of hackers.
What is ASPM?
Definition: Application Security Posture Management is the continuous evaluation of security standards applied to custom and third-party applications running inside of your organization. In this case, applications that are published to Entra ID. The purpose behind ASPM is to establish a mechanism for organizations to identify, mitigate, remediate, and resolve possible vulnerabilities inside of applications so that they can, for the most part, prevent breaches.
Because everything is a word salad and a smorgasbord of acronyms, Cloud Security Posture Management (CSPM) has the same approach as ASPM, except that ASPM focuses on cloud-native applications more so than CSPM.
.png?width=717&height=430&name=Cloud%20Security%20Posture%20Management%20(1).png)
Figure 2. Cloud Security Posture Management
In my previous post, The Anatomy of a Cyber Attack, I talked about how hackers plow through vulnerabilities and spend time inside unsuspecting organizations and what you should be doing from the onset to secure your organization, but there is no silver bullet to any of this. It requires continuous evaluation, continuous mitigation, and continuous administration. Ergo, do it all the time. Yes, the point is to sound like a broken record because that's what it will take to ensure that you at least have a view of how shaky or stiff your application landscape is.
ASPM needs to be viewed as a part of platform security (network, access, data, API) because applications are no longer just being protected by firewalls or perimeter networks. Applications now obtain public endpoints by default. You get to decide what security your application uses, and a lot of times, the provider decides what it looks like. And I’m here to tell you that ASPM is not just for developers. You should, yes, you, the person responsible for Entra ID, you should start caring about ASPM.
What to look for?
Some time back, we had a discussion on Twitter/X about the number of default app registrations that happen when you spin up an M365 tenant. I think the number was 161. One hundred and Sixty-One applications are running in your Microsoft 365 tenant right now, and probably a ton more.
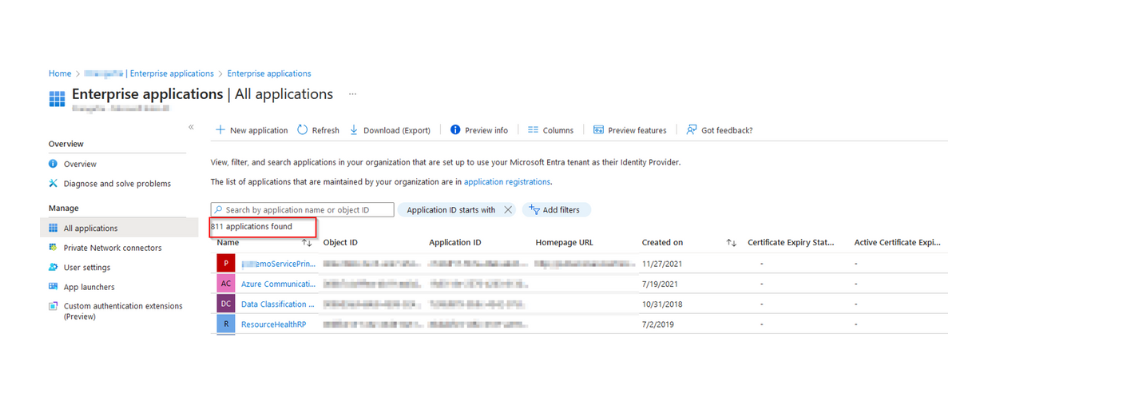 Figure 3. Enterprise Application registrations (showing 811 applications found)
Figure 3. Enterprise Application registrations (showing 811 applications found)
My point is, without looking, how do you know how many apps are running in your tenant? Other questions to ask yourself:
- Do you know which are public, and which are confidential apps?
- Do you have a security standard that both public and confidential apps need to adhere to?
- Do you have a standard for when third-party applications are deployed?
- Do you have a standard when custom applications are being deployed?
These are questions that I have just off the top of my head. There are many other questions that you should be asking not only your internal team but also your application providers, be they third-party providers or your dev team.
Why do you need to know these things?
The purpose behind ASPM, as mentioned before, is to have a concise view of your application landscape in Entra ID so that you can make informed decisions about what you need to do to secure those applications. A solid ASPM strategy offers visibility into:
- Application inventory
- Sensitive data
- Application drift
- Uniformed policy management
- Risk profiling
- Common Vulnerabilities and Exposures (CVE) management and threat intelligence
You need to collate this information to create a functional and rapid remediation strategy for triaging application security in your organization. If you want to learn more about the above, come to our ASPM webinar on Wednesday, March 20th, to find out how applications are deployed in Entra ID, what security really means in Entra ID, how to ensure your applications are secured, and how to continuously evaluate your Application Security Posture.
‘Webinar Wednesday':
Security Hardening for Entra ID Applications – Guidance for Successful ASPM
Wednesday, March 20, 2024 @ 10:00 AM PT / 1:00 PM ET
Speakers: Alistair Pugin and Nicolas Blank
You can register here.
In closing, you need to know about the applications that live in your tenant, what they do, how they talk to internal services, and how they communicate with the outside world. Just because they’re sitting behind an application firewall and or gateway, does not mean they’re secure. Start with a list of all the applications that are running in your tenant. Just doing that, just that, will kickstart your ASPM journey.
Be cool, my ninjas.
Does your Entra ID tenant follow Microsoft-recommended security practices? Sign up to get your score and kickstart your ASPM journey in just a few minutes - get your AppGov Score now!

Written by Alistair Pugin
M365 + Security MVP | Blogger | Podcaster | Speaker | Founder, CEO - YModernize
Alistair has worked in various capacities in multiple verticals from retail-manufacturing to government, spanning 50 to 50000 users utilizing all aspects of pure Enterprise Information Management.
Specialties: 20+ years pure IT, 16 years ECM, Livelink, Zylab, SharePoint, FileNet, etc. IT Pro dabbling in Dev, ECM Consultant, Suffering from Technophilia. Technology Architect specializing in Business Productivity Enrichment.
