Assess, Rate, Remediate Entra ID Applications
May 9, 2025 •Alistair Pugin
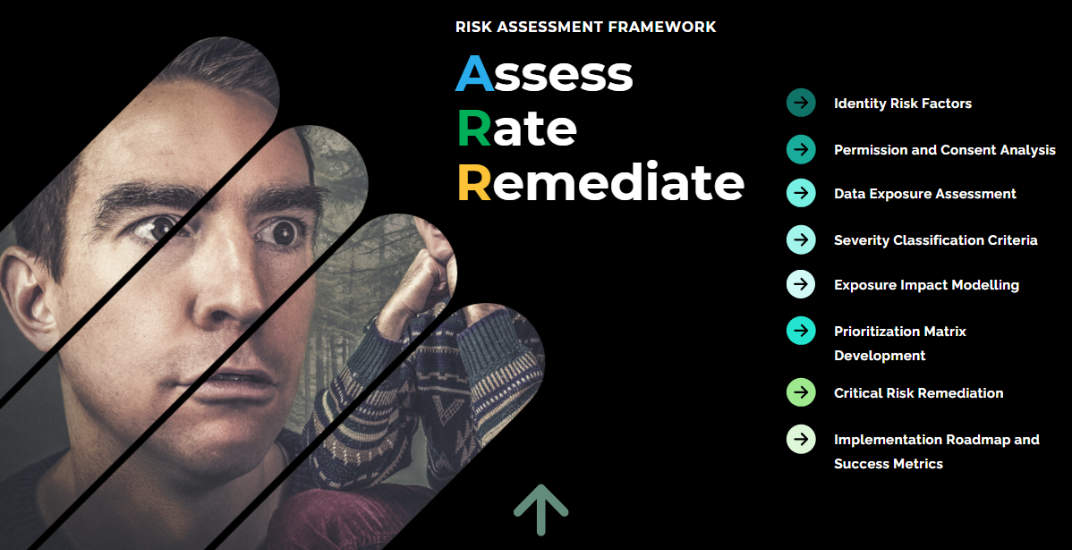
As part of our “Biomarkers” episode, Nic and I added more acronyms to our R.E.A.D. phrase. This time it’s A.R.R., and if you watched the episode, Nic used his “Pirate” voice to describe it.
In part one, we focused on making sure that you have an Identity Management Governance Framework that “Governed’ the 100-day plan that you should follow. Almost like a diet for Entra ID. Yes, it’s a diet. Identity restrictions, watching what you take in, (Roles and Privileges), etc.
Part 2: What you are about to read looks at the other elephant in the room, applications living in your tenant, “rent-free” like Nic always says.
Again, we believe that with a plan, you have a place to start from, a structure to work through, with most importantly, a metrics-based outcome so that you can measure what you need to manage.
Enter: A.R.R.
Comprehensive Plan for Assessing, Rating, and Remediating Entra ID Applications Using Identity Management Governance Framework
Preamble
Microsoft Entra ID applications represent a significant security frontier that requires systematic assessment and remediation processes to maintain a strong security posture. Based on extensive analysis of governance mechanisms and security practices, this article outlines a comprehensive framework for discovering, evaluating, and securing applications registered in Entra ID. The plan addresses critical vulnerabilities that might otherwise remain undetected, with particular attention to application permissions, authentication methods, and access controls. By implementing this systematic approach, organizations can significantly reduce their attack surface, establish ongoing governance, and employ risk-based remediation strategies that prioritize critical vulnerabilities while maintaining operational continuity.
Understanding the Application Security Landscape in Entra ID
The proliferation of applications registered in Microsoft Entra ID environments has created complex security challenges for organizations. Many security teams lack visibility into their application ecosystem, leaving potential vulnerabilities unaddressed. Recent security incidents like Midnight Blizzard have demonstrated how threat actors can exploit poorly configured applications to gain unauthorized access to organizational resources. Additionally, the automated governance capabilities offered by Entra ID Governance provide essential tools for maintaining security, compliance, and operational efficiency in these complex digital environments.
Current Security Challenges
The modern application landscape presents several critical security challenges. Many organizations are unaware of all applications within their Entra ID tenant, creating blind spots in their security posture [2]. This lack of visibility is particularly concerning as applications often have excessive permissions that extend beyond their operational requirements. Furthermore, application governance processes are frequently manual and inconsistent, leading to configuration drift and security gaps over time. Identity-based risks detected by Microsoft Entra ID Protection, including anonymous IP address usage, password spray attacks, and leaked credentials, can directly impact application security if not properly remediated.
The Governance Imperative
Application governance ensures compliance and best practices by establishing systematic oversight throughout application lifecycles. Effective governance improves compliance and risk management by ensuring adherence to regulatory requirements while simultaneously enhancing data security and privacy by implementing appropriate security controls. Microsoft Entra ID Governance addresses these needs by providing robust identity governance capabilities, including automated access reviews, entitlement management, role management, and policy automation. These capabilities form the foundation of our comprehensive assessment and remediation framework.
Discovery and Application Inventory
The first phase of the framework involves creating a comprehensive inventory of all applications registered in your Entra ID environment. This inventory serves as the foundation for all subsequent assessment and remediation activities.
Automated Discovery Methods
Begin by leveraging the Microsoft Graph API to programmatically extract all registered applications from your Entra ID tenant. This approach ensures complete coverage while minimizing manual effort. The API provides detailed application attributes, including application IDs, permissions, owners, and credential configurations. Additionally, Microsoft Entra ID Protection can identify suspicious application behaviors that might indicate compromised credentials or malicious activity [3]. Implement scheduled discovery scans to detect newly registered applications and changes to existing ones, maintaining an accurate inventory over time.
Application Classification Framework
After discovering all applications, implement a structured classification system based on business criticality and data sensitivity. Categorize applications handling sensitive information like financial data, personal identifiable information, or intellectual property as high-priority assets requiring enhanced scrutiny. Identify applications with external exposure, particularly those accessible from the internet or integrated with third-party services, as these present increased risk vectors. Document application ownership and responsibility, ensuring clear accountability for security remediation activities. This classification provides essential context for risk assessment and prioritization decisions.
Creating a Comprehensive Application Registry
Consolidate discovery findings into a centralized application registry that serves as a single source of truth. This registry should include application metadata, authentication methods, assigned permissions, integration points, and ownership information. Implement version control to track changes to application configurations over time, enabling security teams to identify potentially risky modifications. The registry should integrate with your governance processes, supporting access reviews and policy enforcement activities provided by Entra ID Governance.
Risk Assessment Framework
With a comprehensive inventory established, the next phase involves assessing each application's security posture using a structured methodology designed to identify potential vulnerabilities and exposure risks.
Identity Risk Factors Evaluation
Examine each application's authentication mechanisms, looking particularly for legacy authentication protocols that lack modern security features. Assess credential management practices, identifying applications using long-lived credentials instead of more secure certificate-based authentication. Review sign-in patterns to detect anomalous behaviour that could indicate compromise, using Microsoft Entra ID Protection's risk detection capabilities to identify suspicious activities like anonymous IP address usage or password spray attacks. Evaluate the application's integration with Conditional Access policies, which provide an essential security layer for protecting sensitive resources.
Permission and Consent Analysis
Conduct a detailed assessment of each application's delegated and application permissions, noting particularly those with elevated privileges like Mail.ReadWrite or User.ReadWrite.All. Map permissions to business requirements to identify excessive privileges that violate least privilege principles. Review consent mechanisms to ensure appropriate approval processes exist for high-privilege permission grants. Microsoft Entra ID Governance features like entitlement management can help streamline this analysis by providing tools to define and enforce access policies based on business requirements.
Where to start
Data Exposure Assessment
Analyze each application's access to sensitive data repositories, including SharePoint sites, OneDrive storage, and Exchange mailboxes. It's not only applications that have been either manually added or deployed through some automated facility like the Enterprise Applications Gallery or via GitHub/Visual Studio, but also what your tenant came with when you spun it up.
Identify applications with access to regulated information subject to compliance requirements like GDPR, HIPAA, or PCI-DSS. Evaluate data transfer patterns, particularly for applications that might export data to external systems.
Tenant Configuration Evaluation
Review tenant-wide settings that affect application security, including user consent permissions, application registration policies, and API restrictions. Assess administrator role assignments related to application management, identifying potential privilege escalation paths. Evaluate integration with security monitoring solutions to ensure suspicious application activities trigger appropriate alerts. This holistic perspective ensures that individual application assessments are contextualized within your broader security environment.
Risk Rating System Implementation
After completing the risk assessment, implement a standardized rating system to categorize applications based on their security posture and potential impact if compromised.
Severity Classification Criteria
Develop a multi-dimensional severity classification system incorporating factors like data sensitivity, permission scope, authentication strength, and external exposure. Assign weighted values to each factor based on your organization's specific risk profile and compliance requirements. Calculate composite risk scores that provide a quantitative measure of each application's security posture. This approach enables objective comparison across your application portfolio while supporting data-driven remediation decisions.
Exposure Impact Modelling
Model potential impact scenarios for each application based on different compromise vectors, considering both direct and lateral movement possibilities. Estimate potential data exposure volume and sensitivity in case of application compromise. Assess business continuity implications, particularly for mission-critical applications supporting core operations. This modelling exercise provides essential context for prioritizing remediation efforts and allocating security resources effectively.
Risk Visualization and Reporting
Create comprehensive dashboards visualizing application risk across your environment, highlighting critical vulnerabilities requiring immediate attention. Generate detailed reports for application owners explaining identified risks and recommended remediation actions. Develop executive summaries that communicate overall application security posture to leadership without technical jargon. These visualization tools support both tactical remediation efforts and strategic security planning while aligning with the reporting capabilities suggested in ENow's Application Risk Assessment approach within their AppGov platform.
Prioritization Matrix Development
Establish a structured prioritization matrix that combines risk severity with business impact considerations. Balance security requirements with operational concerns to create realistic remediation timelines. Incorporate regulatory compliance factors that might accelerate certain remediation activities. This prioritization framework ensures that security resources address the most critical vulnerabilities first while maintaining a systematic approach to overall risk reduction.
Remediation Strategies for Identified Risks
With applications assessed and rated according to risk, implement appropriate remediation strategies tailored to each severity level and vulnerability type.
Critical Risk Remediation Approach
For applications rated as critical risk, implement immediate containment measures, including temporary access restrictions or enhanced monitoring. Conduct in-depth security reviews with application owners to identify root causes of vulnerabilities. Develop comprehensive remediation plans addressing authentication, permission, and configuration issues. This aggressive approach balances security urgency with operational requirements, ensuring critical applications receive prompt attention.
Authentication Strengthening Methods
Implement certificate-based authentication for all registered applications, eliminating password-based credentials vulnerable to theft or brute force attacks. Enable Conditional Access policies that enforce multi-factor authentication for application access, particularly for privileged operations. Configure credential lifetimes appropriately, ensuring regular rotation without operational disruption. Microsoft Entra ID Protection can help detect authentication risks that might indicate credential compromise, triggering automated remediation workflows.
Permission Rightsizing Implementation
Audit and remove unnecessary permissions from applications, implementing least privilege principles that limit access to essential resources only. Replace broad permissions with more granular alternatives that provide the minimum necessary access. Implement time-bound access for temporary requirements rather than permanent permission grants. This permission rightsizing directly addresses one of the primary attack vectors exploited in application-based breaches.
Governance Process Integration
Establish regular access reviews for application permissions using Entra ID Governance capabilities, ensuring ongoing validation of access requirements. Implement automated policies that detect and remediate configuration drift or policy violations. Create certification workflows requiring owners to periodically revalidate application configurations. This governance integration transforms remediation from a one-time project into an ongoing operational process that maintains security posture over time.
Continuous Monitoring and Preventive Maintenance
After initial assessment and remediation, implement continuous monitoring practices to maintain application security posture and respond to emerging threats.
Automated Risk Detection Implementation
Configure Microsoft Entra ID Protection to continuously monitor for identity-based risks affecting your application ecosystem. Implement automated alerts for critical application configuration changes that might introduce security vulnerabilities. Establish baseline application behaviour patterns and monitor for anomalous deviations indicating potential compromise. These automated detection capabilities provide early warning of potential security incidents, enabling a proactive response before significant damage occurs.
Regular Governance Reviews
Schedule quarterly comprehensive application security reviews using Entra ID Governance tools, validating that all applications maintain appropriate security configurations. Implement automated access reviews for application permissions, ensuring regular validation by appropriate stakeholders. Conduct annual penetration testing against critical applications to identify potential vulnerabilities missed by automated scanning. These governance reviews transform security from a point-in-time activity to an ongoing process embedded in operational practices.
Risk-Based Access Control Enforcement
Implement risk-based policies that automatically require additional verification when suspicious activity is detected, using Microsoft Entra ID Protection's risk detection capabilities. Configure policies that automatically block high-risk sign-in attempts to prevent unauthorized application access. Establish conditional access requirements based on device compliance, location, and other contextual factors. These dynamic access controls provide an adaptive security layer that responds to changing risk conditions in real-time.
Incident Response Integration
Develop application-specific incident response playbooks for different compromise scenarios, ensuring security teams have predetermined action plans. Implement automated containment workflows triggered by high-confidence risk detections from Microsoft Entra ID Protection. Establish clear escalation paths and decision authorities for application security incidents. This integration ensures that the detection of application security incidents triggers appropriate response actions without unnecessary delays.
Implementation Roadmap and Success Metrics
The final section provides a structured timeline for implementing this comprehensive framework, along with metrics to measure effectiveness. This roadmap is to be used in conjunction with our 100-day roadmap and serves as a supplemental approach to improving your overall identity posture. Remember, applications live in Entra ID.
Phase 1: Discovery and Initial Assessment
Begin with a comprehensive discovery of all registered applications using both automated and manual methods to ensure complete coverage. Implement the initial risk assessment methodology, focusing first on externally exposed and highly privileged applications. Establish the application registry with baseline security information for each discovered application. This foundation-setting phase typically requires 4-6 weeks, depending on environment complexity and application volume.
Phase 2: Critical Vulnerability Remediation
Address critical vulnerabilities identified during the initial assessment, focusing particularly on applications with excessive permissions or weak authentication. Implement immediate security improvements for high-risk applications supporting essential business functions. Establish emergency governance processes for newly registered applications to prevent the introduction of additional high-risk configurations. This focused remediation phase typically spans 4-8 weeks and significantly reduces risk for the most critical assets.
Phase 3: Governance Implementation
Deploy Microsoft Entra ID Governance capabilities including access reviews and entitlement management to support ongoing security maintenance. Implement automated policies that enforce security baselines for all applications. Establish regular review cycles for application permissions and configurations. This governance phase typically requires 6-10 weeks and transforms security from project-based to process-based, ensuring sustainable improvements.
Phase 4: Continuous Improvement
Implement comprehensive monitoring using Microsoft Entra ID Protection capabilities to detect and respond to emerging threats. Refine remediation processes based on operational experience and changing threat landscape. Develop advanced metrics that measure security posture improvement over time. This continuous improvement phase represents an ongoing operational commitment rather than a time-bound project phase.
Conclusion
Implementing a structured approach to assessing, rating, and remediating applications registered in Entra ID provides essential protection against increasingly sophisticated identity-based attacks. Organizations can significantly reduce their attack surface and improve overall security resilience by systematically discovering applications, evaluating their security posture, and implementing targeted remediation strategies. Integrating Microsoft Entra ID Governance capabilities enables sustainable security improvements through automated access reviews and policy enforcement [1]. Similarly, Microsoft Entra ID Protection's risk detection capabilities provide essential early warning of potential compromise activities.

Written by Alistair Pugin
M365 + Security MVP | Blogger | Podcaster | Speaker | Founder, CEO - YModernize
Alistair has worked in various capacities in multiple verticals from retail-manufacturing to government, spanning 50 to 50000 users utilizing all aspects of pure Enterprise Information Management.
Specialties: 20+ years pure IT, 16 years ECM, Livelink, Zylab, SharePoint, FileNet, etc. IT Pro dabbling in Dev, ECM Consultant, Suffering from Technophilia. Technology Architect specializing in Business Productivity Enrichment.
