Entra ID: What is it? What can it do for you?
April 18, 2024 •Alistair Pugin

Entra ID. The product formally known as Azure Active Directory, which had its humble beginning as Microsoft Active Directory. The directory service platform that took on OS/2 and Novell’s Netware and dare I say, won. Who would have thought that an application that debuted back in 1999 with the release of Windows 2000 Server edition would have such a monumental impact on all things Identity and Access Management in 2024. 24 years!!! Even in today’s cloud first world, Microsoft is still actively building traditional Active Directory advancements with the upcoming Windows Server 2025 release.
It is, after all, the heart of any, and many applications. We have come a long, long way from it just being a directory services provider. Especially when we look at what Entra ID has become today. The behemoth that is Entra ID. The all seeing, all controlling, all managing eye that is Identity and Access Management, with added spices like Application Registrations, Conditional Access, Device Management (Not to be confused with Intune or Mobile Device Management.)
Like the ending of Dune 2 (Spoiler Alert!) House Atreides has been reborn, set to take overruling all the other houses, so has Entra ID (Muad'Dib) emerged as a culmination of platform resources, ready to rule the Identity and Access Management world.
Naturally, there are many flavors of Entra ID. The Entra ID that gets spun up with you create a Microsoft 365 Tenant, or for customers that do not have Microsoft 365 (very rarely), the Identity service provider into infrastructure services like virtual machines and other cloud native solutions. (Data, App, Container, Serverless).
For now, I want to focus on the bits that you get out of Entra ID Plan 1 as this ships with a Microsoft E3 license.
The Identity Landscape in Microsoft's Cloud
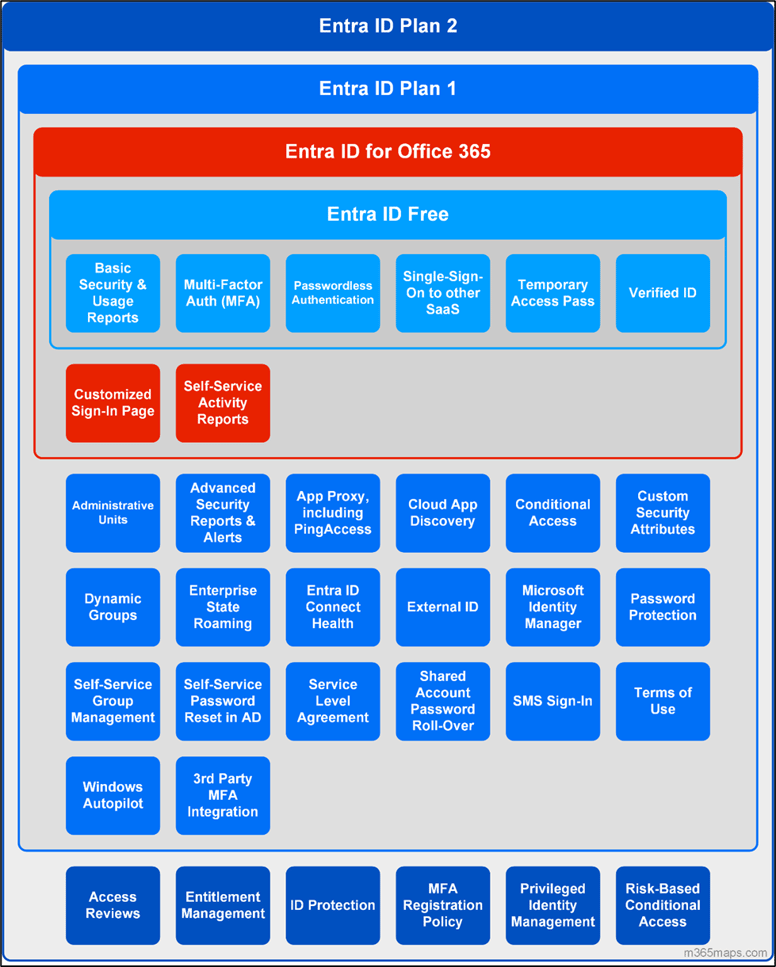
Figure 1: M365 Maps diagram
Just looking at the image above gives me grey hair and anxiety (Oh wait, that’s from my kids and not Entra…) So how does an Identity and Access administrator wrap their heads around the services that the platform provides?
There are so many things listed and they are all connected to identities:
- What identities do
- What identities have access to
- How identities act inside of your tenant
Let me break it down for you into logical groupings:
Identity
Yes, even complex products still do simple things. In this case, you can create accounts that fulfill specific roles. I don’t think I need to elaborate on that. Accounts have access to services in the platform. Those accounts also have roles. Ergo, what the account can do in the service that it has access to.
Figure 2: Entra ID Users
Security
Since identity is the single construct (Primary identifier) into the service, for the most part, this is what gets compromised so naturally, we would want to secure the identity as much as humanly possible. This gets handled in a myriad of ways:
- MFA
- Conditional Access
- Password types
- Security Attributes
- CAS-B
- Administrative units
- Verified ID
Figure 3: Conditional Access
Monitoring and Provisioning
Monitoring and automation of identity management features makes an administrator's life easier. It also provides pivotal information into the identity posture of an organization. These features include:
- Windows Autopilot
- Self-Service features
- Reporting and alerts, including auditing
- Dynamic Groups
- SSO
Figure 4: Usage and Insights
Why are these things important?
Since identities are the heart and soul (A.K.A. The spice) of running anything in the cloud, it is vitally important that it is protected in the same way the Fremen protect planet Arrakis. Since you cannot become a worm or Muad'Dib, at least think of learning how to ride a worm like a Fremen and this is where identity governance principles, and patterns and practices become your new best defense again the other Great Houses.
When developing an identity governance blueprint, the following items must be taken into consideration:
- Defining Clear Policies and Roles:
- Establishing well-defined identity and access management policies tailored to organizational needs.
- Defining roles and responsibilities to ensure accountability and transparency in Entra ID administration.
- Implementing Robust Access Controls:
- Designing and enforcing access control mechanisms to regulate user permissions and minimize the risk of unauthorized access.
- Leveraging Entra ID features such as conditional access and multi-factor authentication to enhance security posture.
- Monitoring and Auditing Mechanisms:
- Implementing robust monitoring and auditing mechanisms to track user activities, detect anomalies, and facilitate compliance audits.
- Utilizing Entra ID reporting and analytics capabilities to gain insights into identity-related risks and trends.
- Addressing User Lifecycle Management Challenges:
- Developing efficient processes for onboarding, offboarding, and managing user identities throughout their lifecycle.
- Automating routine identity management tasks to improve operational efficiency and reduce manual errors.
- Role Mapping and Privileged Access Management:
- Mapping business roles to Entra ID roles to ensure granular access control and alignment with business requirements.
- Implementing privileged access management controls to safeguard critical resources and mitigate insider threats.
- Stakeholder Collaboration and Alignment:
- Fostering collaboration between IT, security, and business stakeholders to align Entra ID governance with organizational goals and priorities.
- Engaging stakeholders in regular communication and feedback loops to adapt Entra ID policies and controls to evolving business needs.
If this is the knowledge you seek - then you must join our webinar next Wednesday, 4/24/24 at 10 am PST which focuses on real world Entra ID Governance. It’s really that simple. We will provide you with a robust approach to building out your Identity Governance Blueprint so that it’s tailored to fit your unique Identity and Access Management requirements.
Do you know what apps are lurking in your tenant? The ENow AppGov Score is a free security assessment tool that will quantify your application governance state quickly. In addition to providing your AppGov Score, the tool will provide a comprehensive Application Governance Assessment report that includes each test, your result and why the test matters. Sign up to get your score and assessment report in just a few minutes - Get Your AppGov Score today!

Written by Alistair Pugin
M365 + Security MVP | Blogger | Podcaster | Speaker | Founder, CEO - YModernize
Alistair has worked in various capacities in multiple verticals from retail-manufacturing to government, spanning 50 to 50000 users utilizing all aspects of pure Enterprise Information Management.
Specialties: 20+ years pure IT, 16 years ECM, Livelink, Zylab, SharePoint, FileNet, etc. IT Pro dabbling in Dev, ECM Consultant, Suffering from Technophilia. Technology Architect specializing in Business Productivity Enrichment.
