Entra ID Application Consent: What Identity Admins Need to Know - Part 1
March 6, 2024 •Matthew Levy

If you are an administrator of a Microsoft Entra ID tenant, you may have encountered the concept of app consent. App consent is the process of a user granting authorization to an application to access protected resources on their behalf. For example, when a user signs in to an app using their Microsoft Entra ID account, they may be asked to allow the app to access their profile information, email, calendar, files, and so on.
App consent can be an empowering way to enable users to access various applications and services with their existing credentials and data. However, it can also pose some risks if not managed properly.
As an administrator, you have the responsibility and the ability to control how users consent to applications and how to revoke or restrict permissions for applications that are already granted. In this article, we will explain what app consent is, why it matters, and how you can control it as an admin.
Why does application consent matter?
App (application) consent matters because it determines what data and resources an application can access and what actions it can perform on behalf of a user or an organization. If an application is malicious or compromised, it could use the granted permissions to access sensitive data, compromise other accounts, or cause damage to your organization as was the case in the latest Midnight Blizzard attack on Microsoft.
To reduce these risks, you should review and manage the permissions granted to applications in your tenant and configure the user consent settings according to your organization's needs and preferences.
What is “consent”?
Consent refers to the act of willingly and consciously agreeing to or permitting something to happen.
App consent
App consent is based on the principle of least privilege, at least it should be, which means that an application should only request and receive the minimum permissions necessary to perform its function. Permissions are divided into two types: delegated and application.
Delegated permissions are granted by a user to an app to act on their behalf. For example, if a user consents to an app that requests Mail.Read permission, the app can read the user's email messages.
Application permissions are granted by an admin to an app to act as itself, without a signed-in user. For example, if an admin consents to an app that requests Mail.Read.All permission, the app can read all email messages in the tenant.
Admin consent
Some permissions require admin consent, which means that only an admin can grant them to an app. These permissions typically allow access to sensitive or organization-wide data or functionality. For example, User.Read.All permission requires admin consent because it allows an app to read all user profiles in the tenant. Admin consent can be useful for applications that need to perform background tasks or access data from multiple users.
Other permissions do not require admin consent, which means that any user can grant them to an app. These permissions typically allow access to less sensitive or individual data or functionality. For example, User.Read permission does not require admin consent because it only allows an app to read the signed-in user's profile.
By default, all users are allowed to consent to applications for permissions that don't require admin consent. For example, by default, a user can consent to allow an app to access their mailbox but can't consent to allow an app unfettered access to read and write to all files in your organization. This can be convenient for users who want to use various apps and services with their Microsoft Entra ID account. However, it can also expose your organization's data to potential risks if users are not careful about what they consent to. Users should be aware of consent phishing emails.
For example, a malicious app could trick users into granting it permissions that allow it to access their data or perform actions on their behalf.
Alternatively, a legitimate app (shadow IT) such as Trello or “Meeting Summaries from Read AI” integrated into Microsoft Teams could request more permissions than it needs or use them in ways that violate your organization's policies or compliance requirements.
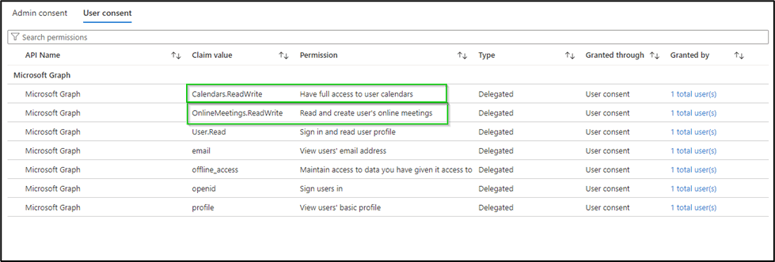
Figure 1: Read AI Teams app permissions could violate policies.
Admin consent also poses some risks of having applications in Entra ID without proper oversight and governance. For example, malicious applications could trick admins into granting them access to sensitive data or resources, or they could request more permissions than they need.
Granting admin consent on behalf of your organization is a sensitive operation, potentially allowing the application's publisher access to sensitive data, or the permission to do highly privileged operations. Therefore, you need to carefully review the permissions that the application is requesting before you grant consent.
Why do some applications ask users to sign in as an administrator to consent and others not?
By default, all users are allowed to consent to applications for permissions that don't require administrator consent.
When a user attempts to sign in to an application for the first time, the system checks whether consent has already been granted for the required permissions. If no record of consent exists, the user is directed to a consent prompt window.
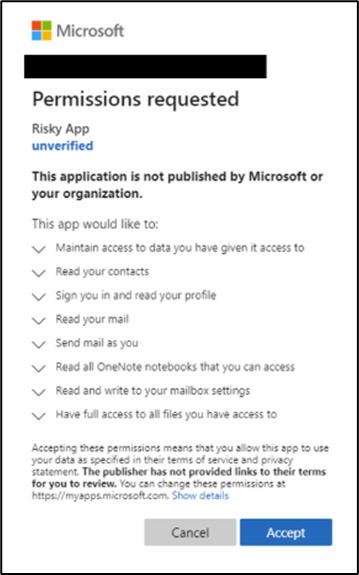
Figure 2: Permission consent prompt for app requiring user consent.
The window for consent prompts can sometimes provide a list as long as my arm of permissions being requested and can be overwhelming for users and admins alike.
If the application only requires delegated permissions and user consent is allowed in the organization's settings, the user can grant consent themselves. However, if the application requires application permissions, or if the organization's settings do not allow users to grant consent for the requested permissions, an administrator must grant consent.
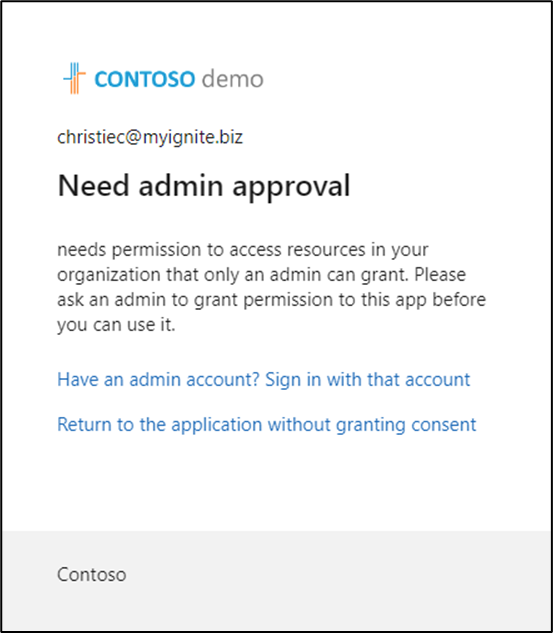
Figure 3: Application requiring admin consent (approval) for the permissions
This is why some applications ask you to sign in as an administrator for consent, while others do not. It depends on the type of permissions the application is requesting and the consent settings in your organization.
What is the risk of apps without admin consent?
The risk of apps without admin consent is lower, in my opinion, than apps that have admin consent because the permissions that would require an admin consent are usually application permissions or more privileged permissions. Admin consent means that the permissions are consented for the entire organization typically and not one or a handful of users. So having more applications in your organization with admin consented permissions could mean that those applications have risky permissions consented for the entire organization.
Of course, there is the risk that users have consented to permissions without a full understanding of the implications and so controlling user consent is still important. You should classify permissions as low or high impact and allow user consent only for low impact permissions.
Admin consent on the other hand is a sensitive action that requires vigilance and understanding. Only well-trained admins should be allowed to consent on behalf of the organization.
Knowing which app permissions have been approved by an administrator and whether or not those permissions are actually required is more of a concern these days for an Entra ID administrator.
What's Next?
Application consent is something that most Entra ID administrators are not deeply familiar with unless you have a developer background. It’s important to understand the different permission types, requests and consent options. In the first part of a two-part series, I gave you some insights into Microsoft Entra ID Application Consent. I explained why as a Microsoft Entra administrator, it is important to know the risks of users and administrators alike granting consent to an application's permission requests without fully understanding the difference between delegated permissions and application permissions. I also discussed the difference between user consent and admin consent.
As an Identity administrator responsible for an ever-moving target, you need processes and tools to help you govern and secure these application permissions. In part 2, I will provide recommendations and processes for governing Microsoft Entra ID Application permissions and consent. I also demonstrate how Enow’s AppGov Accelerator accelerates the process of drawing reports and assists in focusing on risks in the environment for you to address.
Do you know what apps are lurking in your tenant? The ENow AppGov Score is a free security assessment tool that will quantify your application governance state quickly. In addition to providing your AppGov Score, the tool will provide a comprehensive Application Governance Assessment report that includes each test, your result and why the test matters. Sign up to get your score and assessment report in just a few minutes - Get Your AppGov Score today!

Written by Matthew Levy
Microsoft Security MVP | Principal Architect @NBConsult | Speaker | Blogger. I am an Identity and Access Solutions Architect for NBConsult, a leading IT service provider in South Africa. I have 20+ years of experience in Microsoft enterprise technologies. I am passionate about Identity Governance and how it can help organizations achieve better security, compliance and productivity. I write blogs where I share my insights and tips on Application Governance.
