Entra ID Application Consent: What Identity Admins Need to Know - Part Two
April 16, 2024 •Matthew Levy

In the first part of this two-part series, I explained the principles that apply to Microsoft Entra ID Application Consent, something most admins aren’t very familiar with unless you come from a developer background. As a Microsoft Entra ID administrator, it is important to know the risks of users and administrators alike granting consent to an application's permission requests without fully understanding the difference between delegated permissions and application permissions; it’s also important to note the difference between user consent and admin consent.
This second part will provide you with some best practices, tips and recommendations to govern and secure your Microsoft Entra ID application landscape. Let’s get started!
Configure user consent settings
It is highly recommended to limit user consent to specific low-risk permissions and verified publishers through user consent settings in Microsoft Entra admin center or via Microsoft Graph PowerShell or Microsoft Graph API. There are three consent settings you can configure for all users:
Setting #1: Allow user consent for apps
This is the least restrictive setting, which allows all users to consent for any app to access the organization’s data. Allowing user consent by default opens the door to potentially malicious applications to request access to sensitive data, speculated to have been part of the Midnight Blizzard attack on Microsoft, also known as Illicit Consent Grants.
Setting #2: Allow user consent for apps from verified publishers for selected permissions
This option allows limited user consent only for apps from verified publishers and apps that are registered in your tenant, and only for permissions that you classify as low impact. Remember to classify the permissions you deem low impact to which you want to allow users to consent to. Microsoft actually provides some permissions you can use to get started that are considered low impact. It’s a good idea to start with these permissions defined and classified as your low-risk permissions, starting with the least restrictive.
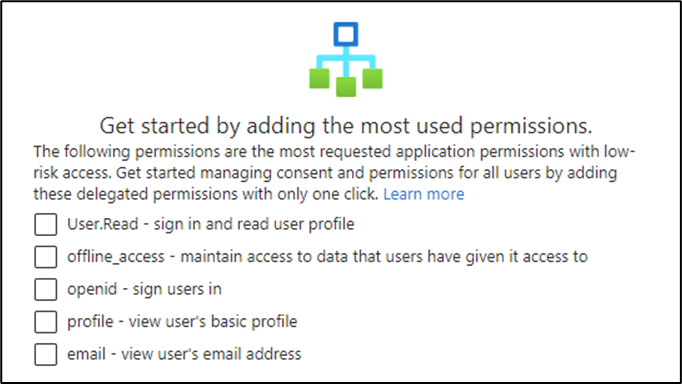
Figure 1: Microsoft recommended low-risk permissions (delegated)
Any application requesting any of these low-risk delegated permissions will allow the user to consent. Applications from verified publishers are still subject to the permission classifications you set, but verification helps with transparency and users can identify apps that are developed by trusted publishers by looking for the blue verified badge on consent requests.
Setting #3: Disable user consent for apps.
This option disables all future user consent operations to applications. Users will not be able to grant permissions to any applications unless an administrator has previously granted consent on behalf of the organization.
While managing app consent is important for security and compliance reasons, it may also have some drawbacks or challenges. Limiting or disabling user consent may reduce the flexibility and productivity of your users who need access to certain applications for their work or personal needs. Some users may feel frustrated or restricted by the policies that prevent them from using the apps they want or need.
Therefore, before making any changes to your app consent settings or revoking app permissions, you should consider the impact and implications for your users and your organization and balance the security and productivity needs. You should also communicate clearly with your users about the reasons and benefits of the policies and provide them with guidance and support on how to use the applications safely and responsibly.
Configure the admin consent workflow
With the user consent either limited or disabled, users need a secure way to request admin consent for legitimate applications. Admin consent workflow is a feature that allows you to require approval from an administrator before granting permissions to an application. This way, you can ensure that only authorized and necessary applications are granted access to your organization's data and resources.
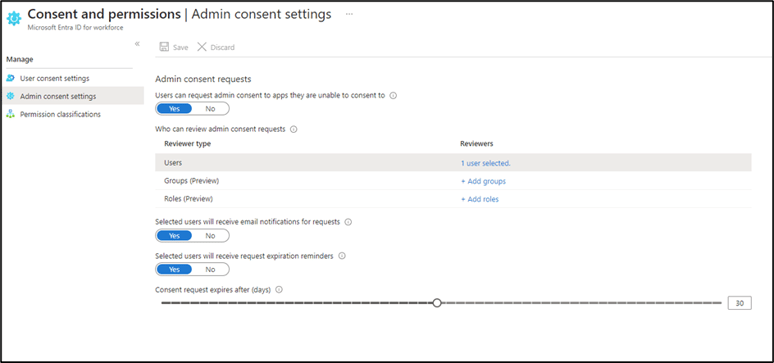
Figure 2: Admin consent settings in Entra portal
Once you enable admin consent workflow, users who try to grant permissions to an application that requires admin consent will see a message that they can request approval from an administrator. The selected administrators will receive an email notification with a link to review and approve or deny the request. The user will also receive an email notification with the outcome of their request. The settings in the above screenshot reflect the situation referenced.
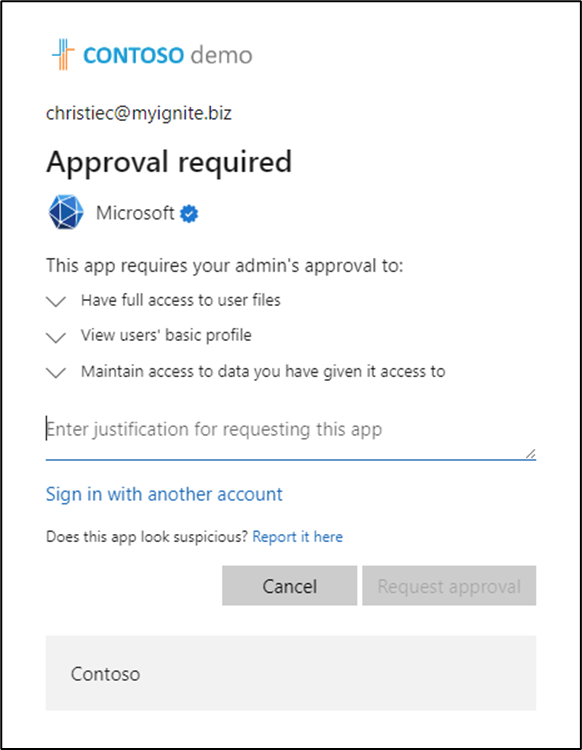
Figure 3: User required to provide justification for admin consent before sending request to an admin
Once the user enters the justification, the user is notified that the request is pending admin consent.
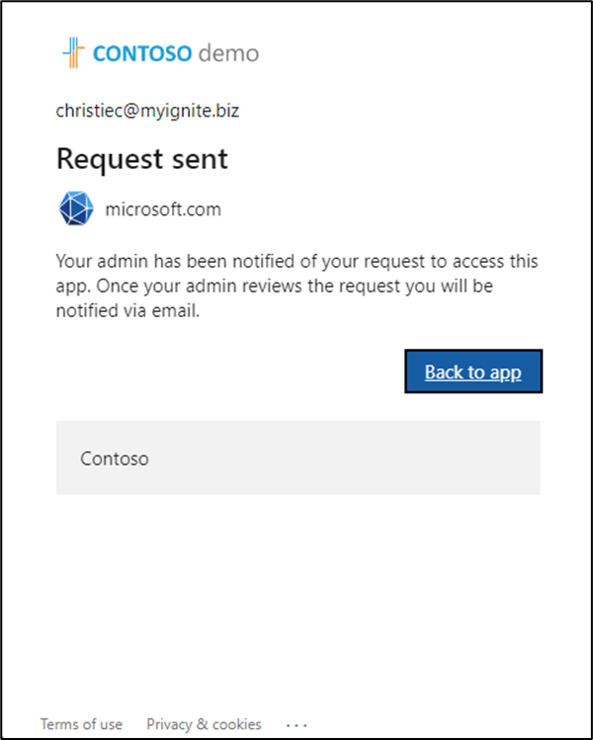
Figure 4: Admin consent workflow notifies the user of the pending request.
The admin experience for the request is shown in the following screenshot. Admins need to review all the permissions before approving them because they will be consented to for the entire organization. For example, by default, when you provide admin consent to an app the properties are ‘Assignment Required’ set to ‘No’, and ‘Visible to Users’ set to ‘Yes’. This means that it is visible and usable for everyone in the organization. If not everyone needs access, then User assignment should be configured, and a group should be created to limit the visibility and usage of an admin-consented app.
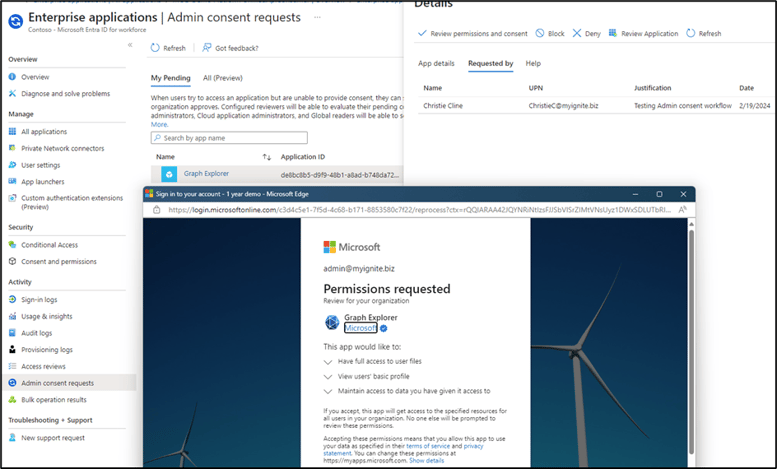
Figure 5: Admin consent portal experience.
Create an access package
If you have an application that requires higher levels of permissions, or you block user consent outright, it might be worthwhile pre-consenting to the application as an administrator and limiting who can access the application using an access package in Microsoft Entra’s Entitlement management. Note that you can achieve the same outcome using group membership combined with the ‘user rights assignment required’ option.
Entitlement management is an identity governance feature that allows organizations to manage identity and access lifecycle at scale, by automating access request workflows, access assignments, reviews, and expiration.
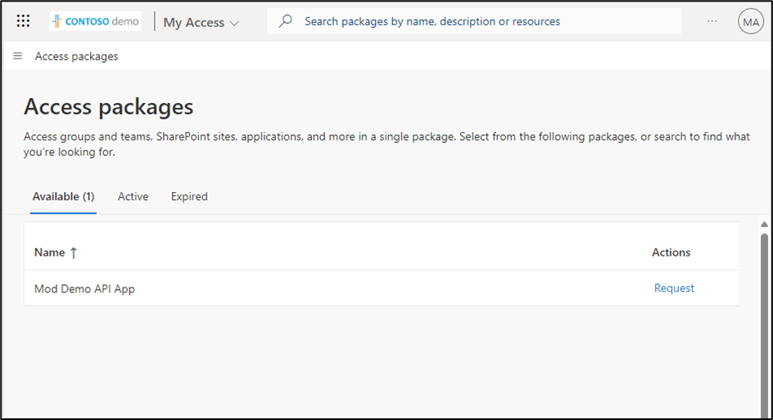
Figure 6: Access package containing an app with pre-consented permissions.
With entitlement management, you can control who can get access to pre-consented applications with multi-stage approval and ensure users don't retain access indefinitely through time-limited assignments and recurring access reviews.
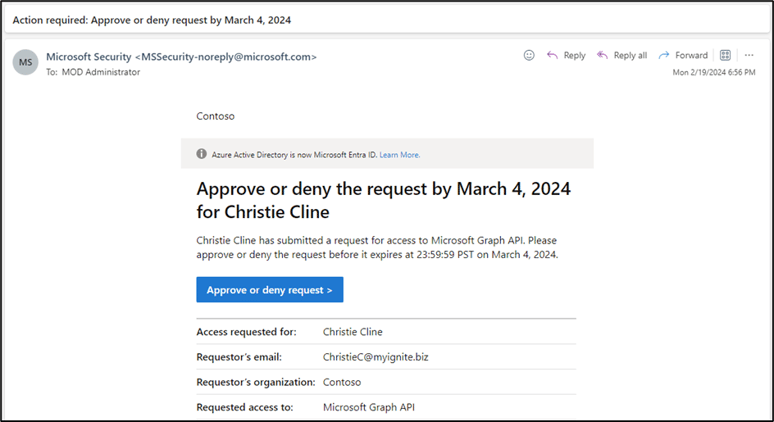
Figure 7: User access package request for admin to approve.
To use entitlement management, you will require either a Microsoft Entra ID P2 or Microsoft Entra ID Governance License, OR the Enterprise Mobility + Security (EMS) E5 license. Read more about how to create Access Packages in Entitlement management at https://learn.microsoft.com/en-us/entra/id-governance/entitlement-management-access-package-first
Review the permissions granted to applications and revoke them if necessary
As an administrator, you have several options to control how users consent to applications in your tenant. Once you’ve implemented your consent policies, you should review existing permissions and revoke risky permissions where possible. You can use the Microsoft Entra admin center or the Microsoft Graph API to review the permissions granted to applications in your tenant. After which you can plan to revoke excessive permissions or remove the applications.
Natively, this is not a trivial task. You have to go into each application one by one and enumerate the permissions that have been consented to individually, and revoke the permission - individually.
To do this:
- Sign in to the Microsoft Entra admin center as at least a Cloud Application Administrator.
- Browse to Identity > Applications > Enterprise applications > All applications.
- Select the application that you want to restrict access to.
- Select Permissions.
- Under Admin consent, select the permission’s context menu, Revoke Permission.
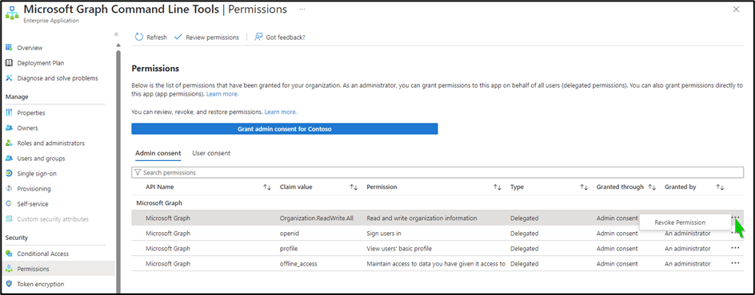
Figure 8: Revoking admin consented permission individually.
This will revoke the admin consent for the application and remove its access to any resources that require admin consent. You can't revoke permissions in the User consent tab using the portal. You can only revoke these permissions using Microsoft Graph API calls or PowerShell cmdlets.
Note that this will not affect the user consent for the application, which means that users can still re-consent to permissions that do not require admin consent.
Alternatively, you can do this on a per-user basis. By going to each user and enumerating the applications that have privileges that either the user has consented to, or an admin has consented to. This is also quite tedious and time-consuming.
Figure 9: MOD Administrator interface.
You can use the Microsoft Graph PowerShell command “Remove-MgOauth2PermissionGrant” to delete a delegated permission grant, but you need to know the unique identifier of the oAuth2PermissionGrant.
However – there are third-party tools out there that can quickly and easily run these reports for you without having to go through the manual process with Microsoft Graph PowerShell commands.
ENow’s App Governance Accelerator is a software solution designed to help organizations gain and maintain control over their Microsoft Entra ID applications. The software helps admins quickly identify risky apps and determine the owner and whether they are being used so you can remove them or stop them from accessing corporate data.
The free AppGov Score will provide you with the number of high-risk applications in your tenant and will report the percentage of apps that are without admin consent.
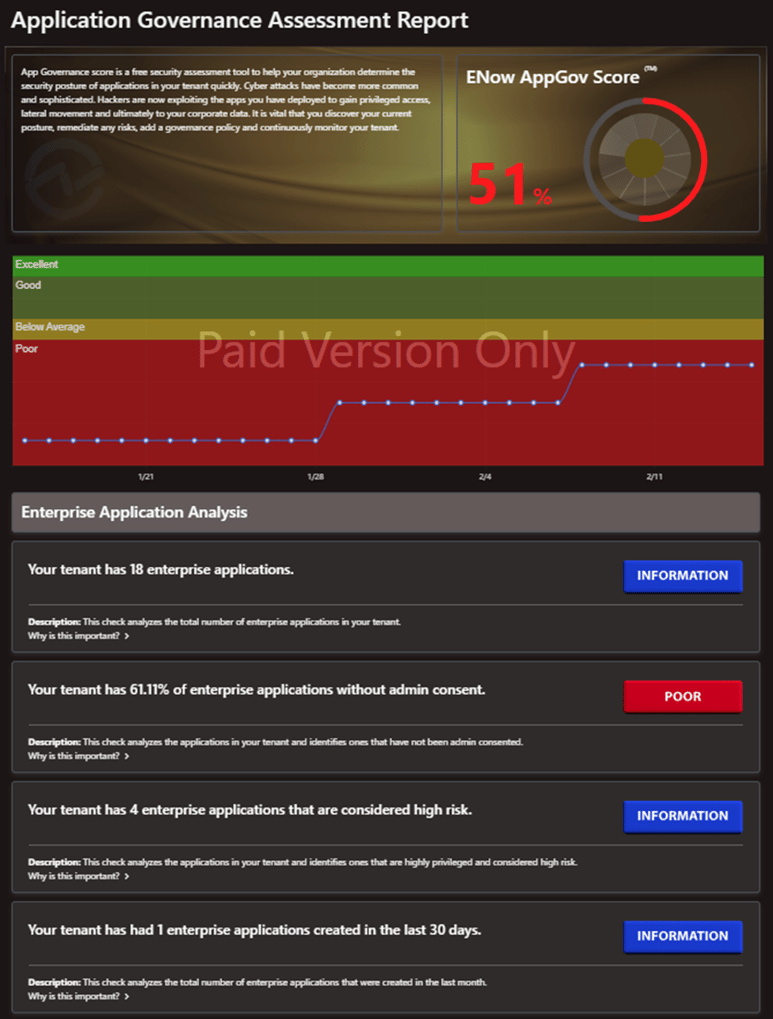
Figure 10: ENow AppGov Score Dashboard
One caveat to consider, however, is that an application may have more permissions than the user delegated as “owner.” Depending on the application permissions it could be abused by threat actors for privilege escalation attacks if they are able to impersonate the application. The AppGov Score from ENow can show you how many ownerless apps are in your tenant in a matter of minutes.
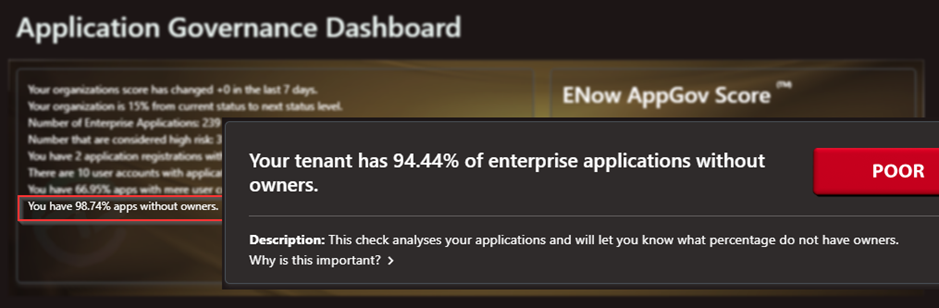
Figure 11: AppGov Score reports percentage of Enterprise apps without owners
There are different license levels of the paid version of the software. You can create an exportable report of those applications so you can view detailed information such as Owner, API Permissions consented for either by users or an administrator, and even sign-in activity details to help you establish if the app is in use or not. After reviewing the permissions and contacting the owners, you can then move to revoke the permissions where possible.
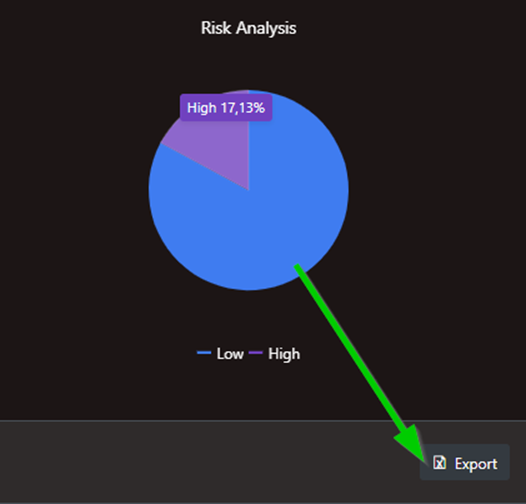
Figure 12: Risk Analysis report with export feature in App Governance Accelerator
By exporting the list of high-risk apps in a test environment and using the power of Excel’s pivot tables, you can see the risky permissions that have been consented to by an administrator for the respective apps. I have highlighted the risky permissions in the screenshot for illustration purposes.
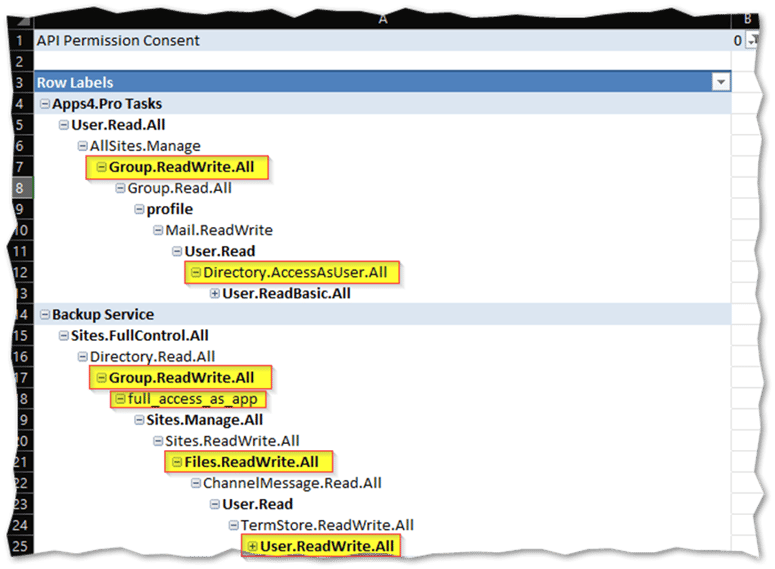
Figure 13: Excel report of risky permissions per app
Because there are thousands of permissions in the system and each business has its own distinct perception of risky permissions, Microsoft provides a list of commonly misused permissions they deem highly privileged. There is even a handy CSV file as part of the MSIdentityTools GitHub repository. Fortuitously, ENow’s App Governance Accelerator has this already built into the code. Ultimately, it is up to you and your organization to decide which permissions to look for and classify as risky permissions.
After exporting the report, you can use it to reference the owner column for the respective apps and contact the owners to find out more about the application if need be. Incidentally, as part of your application governance framework, you would want to ensure that newly consented apps have at least one owner specified for future reviews.
One of the most common problems I find in existing tenants these days is that most Enterprise applications do not have a specified owner. This means most Enterprise apps have been registered by an admin, and no one has been delegated as the owner of the respective apps. It's also important to note that you cannot set a group as an owner, which would be ideal. As a best practice, it is recommended to ensure there are at least two owners, where possible, to avoid having ownerless apps. An owner can also be added to the 'Notes' field if security is a concern, which will also be helpful in fortifying your app security environment.
Recommendations to admins
To govern and secure your Microsoft Entra ID app landscape, as an administrator, you need to:
Configure App Consent Setting- Create a user consent policy that either blocks users from consenting to applications altogether or only allows users to consent to applications with low-risk permissions.
- It is strongly recommended that you create an admin consent workflow for applications that require admin consent, but make sure that admins are aware of the risks and implications associated with consenting for the entire organization.
- Audit all the applications where users have consented to permissions themselves (user consent) and where an administrator has granted consent on behalf of multiple users or the entire organization (admin consent), especially those permissions that could be risky and grant access to sensitive resources such as ReadWrite.All for example.
- Contact the application's owners, either internal owners or third parties that provide the application to your organization, and establish if those permissions are really necessary.
- Revoke app permissions. Be aware that revoking app permissions may cause the application to stop working properly or break existing integrations or workflows.
- Block end-user registration of apps in your tenant.
- It goes without saying, but ALL admins should have phishing-resistant MFA and be required to satisfy MFA from a managed device before consenting to app permissions.
- Educate users and admins about the importance of reviewing the consent prompt and understanding the implications of granting consent to applications in the future.
- Finally, you may have some applications that you, as an admin, must consent to and that have risky permissions. In these cases, it is vital to monitor and track who has access to the application. If you have Entra ID P2 or Identity Governance licenses, consider creating access packages for those applications, and be sure to use the Access Reviews feature.
In conclusion, auditing and reviewing permissions consents requires dedicated time and effort. The security of the tenant depends on a well-prepared process for reviewing apps. A process for assigning owners to applications is also important to help you govern applications in your tenant.
As far as consent policies are concerned, admins may lose visibility into which applications have been granted consent by individual users. Without proper control mechanisms, it becomes challenging to manage and audit application permissions manually. For organizations that have many users, high app usage, or both, and don’t have the resources to sift through manually, there are tools out there like ENow’s App Governance Accelerator that automates reports and recommendations for you.
Admin consent is more secure and consistent than user consent, as it ensures that all users have the same level of access and protection for their data and resources. Configure the admin consent workflow regardless of your user consent settings so users can request applications from an administrator and create that visibility, too.
Whether to allow user consent or require admin consent depends on the specific needs and security posture of your organization. It's a balance between user convenience and data security.
Managing app consent may require additional time and effort from the administrators who need to review and approve or deny requests, monitor and audit app usage, and communicate and educate users about the policies and best practices. Again, ENow’s AppGov suite of reports and alerts will reduce the manual scripting effort.
Do you know what apps are lurking in your tenant? The ENow AppGov Score is a free security assessment tool that will quantify your application governance state quickly. In addition to providing your AppGov Score, the tool will provide a comprehensive Application Governance Assessment report that includes each test, your result and why the test matters. Sign up to get your score and assessment report in just a few minutes - Get Your AppGov Score today!

Written by Matthew Levy
Microsoft Security MVP | Principal Architect @NBConsult | Speaker | Blogger. I am an Identity and Access Solutions Architect for NBConsult, a leading IT service provider in South Africa. I have 20+ years of experience in Microsoft enterprise technologies. I am passionate about Identity Governance and how it can help organizations achieve better security, compliance and productivity. I write blogs where I share my insights and tips on Application Governance.
