Five Things Identity Admins Can Do to Harden Security Around Entra ID Applications
March 27, 2024 •ENow Software

On March 20th, ENow held a webinar on Security Hardening for Entra ID Applications, hosted by Microsoft Security MVP Alistair Pugin and Microsoft MVP/MCM/MCSM Nicolas Blank. They expertly broke down each of the various components of ASPM, providing clarity through best practices that Identity admins and their teams that can implement immediately.
If you’re an Identity admin and haven’t hopped on the Application Security Posture Management (ASPM) bandwagon yet, your organization could be headed for a rude awakening. Yes, ASPM is nothing new, but for Entra ID admins it can be a cumbersome undertaking, albeit a critical one to your organization’s overall security. Once an application is deployed, organizations must understand how that application was deployed and what security patterns and practices are required to ensure that the application is secure.
Why is an ASPM strategy for Entra ID apps important?
The objective behind ASPM is to provide guidelines to help you and your team gather the necessary information in a structured way that will put your application landscape in Entra ID in perspective. Solid ASPM strategies provide the optics you need around:
- Application inventory
- Sensitive data
- Application drift
- Uniform policy management
- Risk profiling
- Common Vulnerabilities and Exposures (CVE) management and threat intelligence
You and your team must compile data pertaining to the above areas, specific to your tenant and Entra ID application landscape, to create a functional and rapid remediation strategy for triaging application security in your organization.
But wait - What exactly is ASPM again?
Definition: Application Security Posture Management is the continuous evaluation of security standards applied to custom and third-party applications inside of your organization. In this case, applications that are published to Entra ID. The purpose behind ASPM is to establish a mechanism for organizations to identify, mitigate, remediate, and resolve vulnerabilities inside of applications so that they can, for the most part, prevent breaches.
Data breaches are all the rage these days and are rapidly increasing in popularity. Agency statistics show month-over-month increases; see for yourself:
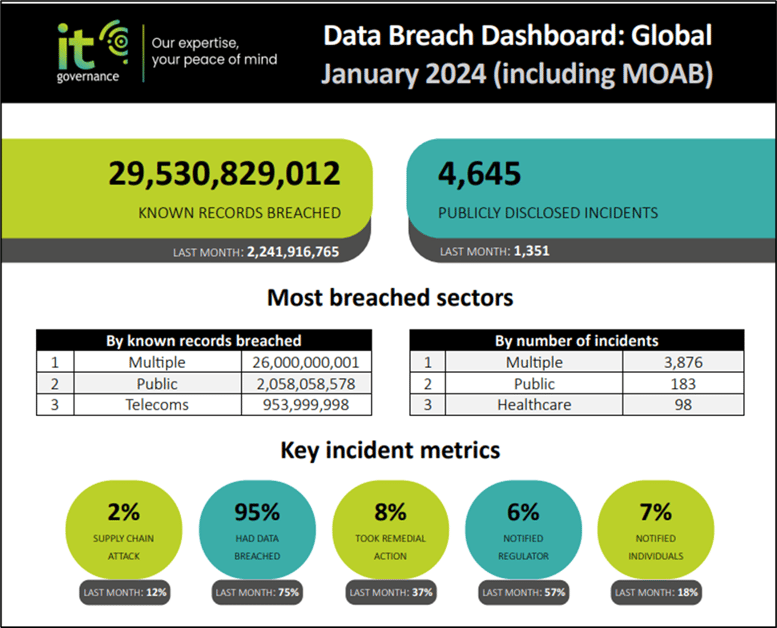
Figure 1: Data breach dashboard from January 2024 (https://e.grci.group/l/500371/2024-02-05/5n2f9y/500371/1707147257IMn8r4Jp/Data_Breach_Dashboard_UK_Jan_24.pdf)
Additionally, the FBI recently released an alarming report indicating a consistent year-over-year rise in BEC (Business Email Compromise) crimes:
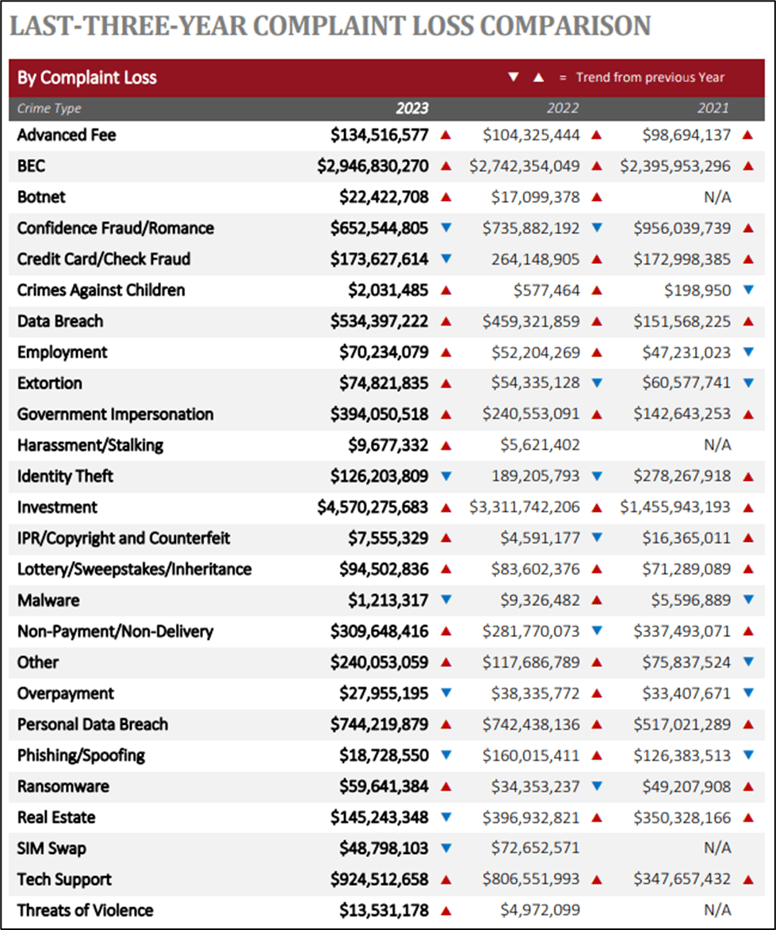
Figure 2: FBI Internet Crime Report 2023 (https://www.ic3.gov/Media/PDF/AnnualReport/2023_IC3Report.pdf)
As we all know, no organization is exempt from insecure app breaches, not even Microsoft. Good news is, it’s not too late to join the ASPM party, and we have some tips that can help get you in.
Now, we won’t recap the entire webinar here, no, no, no! But here are some takeaways, and for more detail into the nitty gritty of each, well, you’ll just have to do your due diligence and watch the On-Demand recording 😊
#1 – Understand your role in app security
First things first, you need to understand your role as an Identity admin. Identity and access management now “sits” in this new grey area of the cloud and Entra ID, so you need to be aware of what you and your team are responsible for managing. You might be asking yourself, “Why me? Doesn’t this fall under the developers?”

Yes, DevSecOps is and will still be a “thing” and crucial in the spectrum of ASPM, but applications aren’t entirely in their purview anymore. Since Identity admins now “own” Entra, you need to be well versed in these things called Application Registrations/Enterprise Applications, and that may be new to many Identity people.
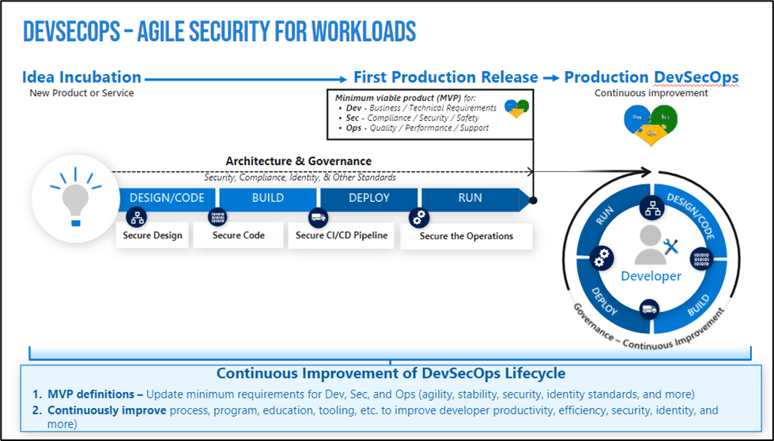
The webinar also provided some very helpful visual mapping tools around the Security Operations Microsoft Cybersecurity Reference Architecture, which we encourage you to review.
#2 – Understand App Deployments and how to manage Entra ID applications
If you didn’t get the memo already, it’s important to know that apps can be deployed without you even knowing about them. These are typically 3rd party applications that get deployed into your environment, such as the Teams app, right "out of the box" and straight from the Team app store. Of course, the account deploying the app would need permissions or would have been granted admin consent permissions to do this, but the fact that this is possible should raise some alarm bells.
Again, it is imperative that Identity admins fully understand the fundamentals of Microsoft Entra ID - tenants, app registrations, enterprise apps, and consent – and how they all function together, so you can elevate your organizations' security posture by implementing strategies to protect your cloud data.
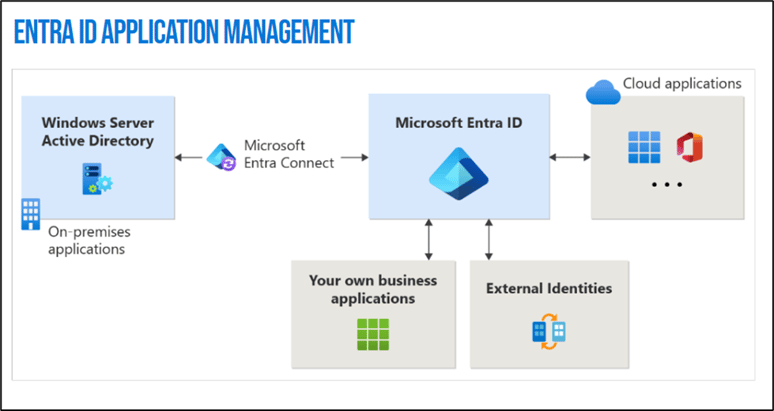
It is also possible to publish an application with zero authentication and/or security, because the option to use an authentication provider is optional. Therefore, it is your responsibility to ensure the authentication configuration is done correctly.
#3 – Know Your Applications
Take inventory. Profile and classify your apps. How many are third-party apps? How many are custom applications? How many apps are without role assignments? How many are Public, and do you have Public Client Flows properly secured? How many are Confidential? Because different security policies apply. Note the app infrastructure because again, different security policies apply to Traditional (on-premises) apps vs. Cloud Native.
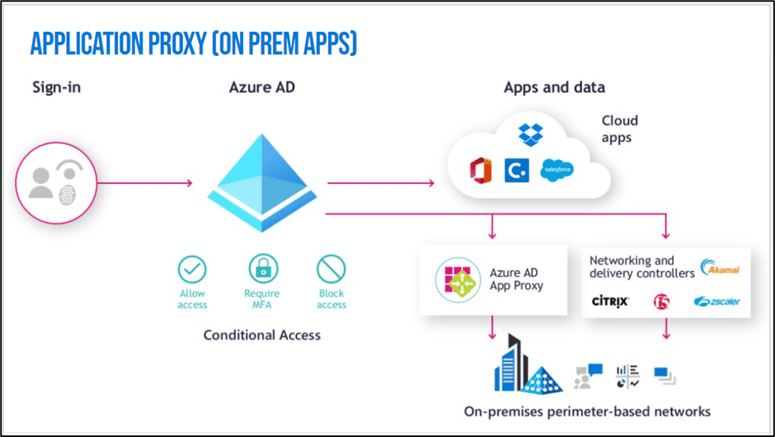
#4 – Existing Security Frameworks are your friend
Between NIST, CIS, and ISO, – there are plenty of trusted standards and benchmarks they provide specifically to help organizations stay secure, offering numerous resources you can lean on for guidance along the way.
Also, let’s not forget about that little thing called Zero Trust! “Assume breach, least privilege,” and how those principles factor across the Microsoft Identity Platform.
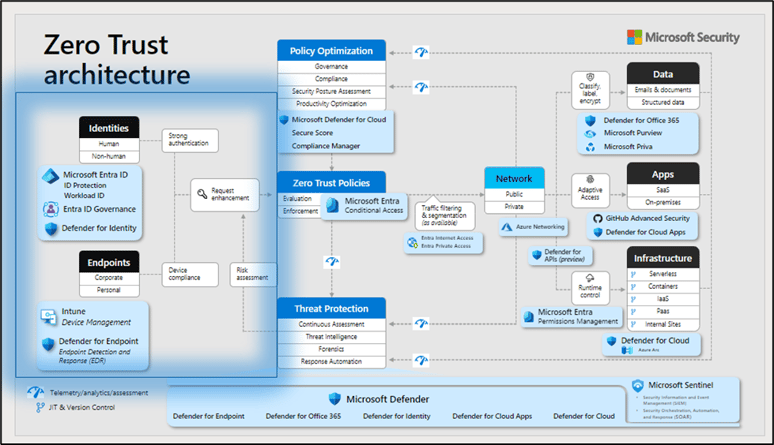
And yes, that’s a busy slide and you probably can’t read all the details. You’ll want to watch the ODW recording anyway to have Nicolas Blank walk and talk you through it.
#5 – Continuously Evaluate, Continuously Assess
Take Alistair Pugin’s advice and develop an AppSec Checklist. Make sure your team can check all these boxes, and confidently say they’ve followed all ASPM security protocols:
- Application Interaction
- Application Security
- Application Integration
- Application Visibility

Continuous Evaluation/Continuous Assessment (CE-CA) can only be achieved with proactive and ongoing monitoring of your Entra ID application estate. This isn’t a one-and-done approach because your tenant and the apps within it will continuously evolve.
Take Control of Your Security Landscape
The ENow App Governance Accelerator 2.0 empowers organizations to take control of their security landscape, equipping them with the tools needed to illuminate potential threats and streamline app management in Entra proactively. As the threat landscape continues to evolve, staying ahead of the curve is not just a priority—it's imperative. With ENow, you can fortify your defenses and navigate the digital terrain with confidence.
The ENow App Governance Accelerator 2.0 release is now in GA, equipped with advanced features designed to fortify your defenses against OAuth-related attacks and streamline app management within Microsoft Entra ID.
For a comprehensive overview of all features and improvements introduced in this release, please contact us to schedule a call.
Stay secure. Stay ahead.
Do you know what apps are lurking in your tenant? ENow App Governance Accelerator helps organizations quickly get in control of their Entra ID apps and remain in control. It enables them to understand their current security posture, what they need to do to improve it, and accelerates making the necessary changes to get to their desired state. Get the ENow App Governance Accelerator Platform today!

Written by ENow Software
ENow protects and optimizes Microsoft 365, Copilot, and Entra ID, giving modern IT leaders clarity and simplicity to manage complex environments. From proactive monitoring to license optimization, adoption, and identity governance, ENow enables IT teams to manage, scale, and secure their Microsoft environment with confidence; all in one place, without the chaos.
