The Hidden Risks of Entra ID Application Ownership (Part 1)
November 20, 2025 •Glenn Van Rymenant
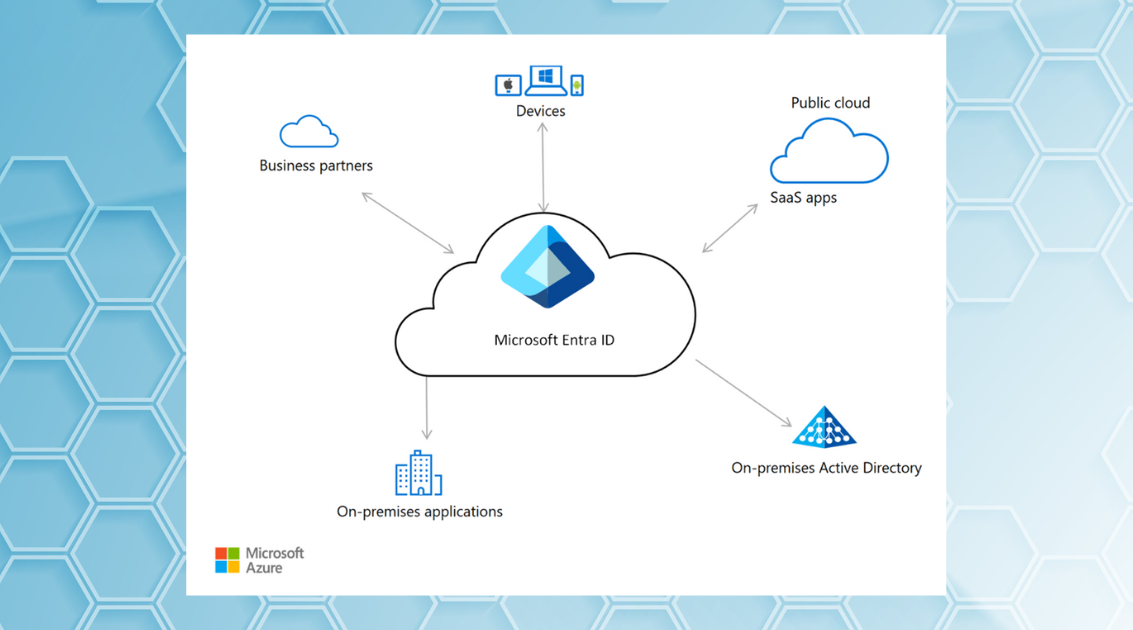
Assigning ownership to your application and service principal objects in Entra ID might seem like good governance, but it introduces significant...
Read MoreMicrosoft Entra ID App Governance: How to Clean Up Apps Without the Chaos
August 22, 2025 •Matthew Levy
Cleaning up applications in Microsoft Entra ID (formerly Azure AD) is a critical part of application governance. Without the right data and process,...
Read MoreCommvault Metallic Vulnerability (CVE-2025-3928) Exposed OAuth Credentials
August 8, 2025 •Nicolas Blank
Backup applications are designed to protect your data, but when over-permissioned, they can become high-value targets for threat actors. I’ve been...
Read MoreIn Microsoft Entra ID, enterprise applications without assigned owners, often referred to as "ownerless apps" pose significant risks to...
Read MoreReclaim Control: Automate Entra ID Governance with ENow App Governance Accelerator 3.0
July 15, 2025 •ENow Software
In today’s enterprise environments, Microsoft Entra ID is at the heart of access, identity, and application connectivity. But with hundreds or...
Read MoreSecuring Workload Identities in Entra ID: A Practical Guide for IT and Security Teams
July 1, 2025 •Alistair Pugin
In part 1 of this blog series, we discussed what workload identities are, their risks, and the consequences they cause if not monitored. In this blog...
Read MoreMicrosoft Disables User Consent By Default, Are You Ready For MC1097272?
June 27, 2025 •Sander Berkouwer
On June 17th, in its Message Center, Microsoft announced a major upcoming change in the context of its Secure Future Initiative (SFI) that has a high...
Read MoreProtecting Workload Identities: Mitigating Risks in Microsoft Entra ID
June 20, 2025 •Alistair Pugin
Introduction: The New Frontier of Cloud Security
Read MoreIn Microsoft Entra ID, enterprise applications and app registrations are critical components for managing access to SaaS applications, internal...
Read MoreWhat has the world come to when "service" accounts can be compromised? It's no longer just someone's identity that gets exploited; the "unattended"...
Read More


%20Exposed%20OAuth%20Credentials%20%20.png?height=630&name=Commvault%20Metallic%20Vulnerability%20(CVE-2025-3928)%20Exposed%20OAuth%20Credentials%20%20.png)



.png?height=630&name=Microsoft%20disables%20user%20consent%20by%20default,%20are%20you%20ready%20for%20MC1097272%20(1).png)